الأكثر طلباً




Previous
Next
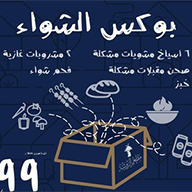
لتجربة شواء إستثنائية!
اطلب بوكس الشواء الخاص بك الآن
6 أسياخ مشويات مشكلة
صحن مقبلات مشكلة
2 مشروبات غازية
فحم شواء
خبز
99 ريال فقط


آراء العملاء
5/5
خدمة سريعة ومذاق
مميز، المفضل عندي!
سالم السعيد
5/5
خدمة سريعة ومذاق
مميز، المفضل عندي!
سالم السعيد
5/5
خدمة سريعة ومذاق
مميز، المفضل عندي!
سالم السعيد