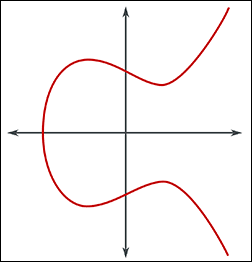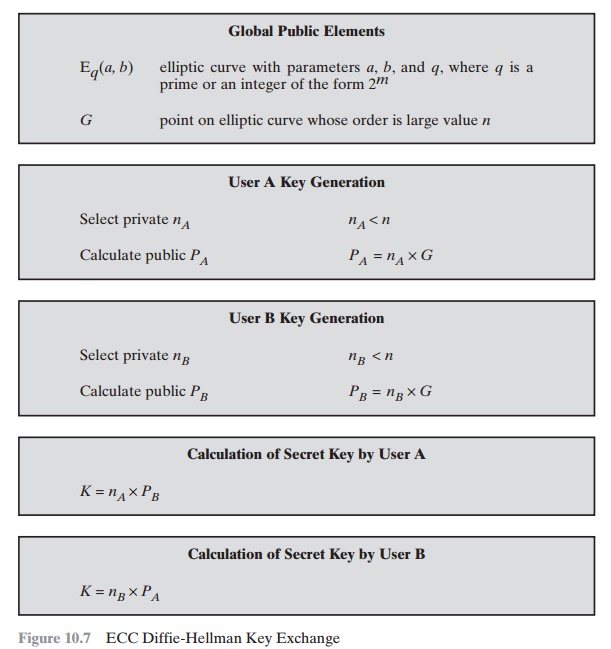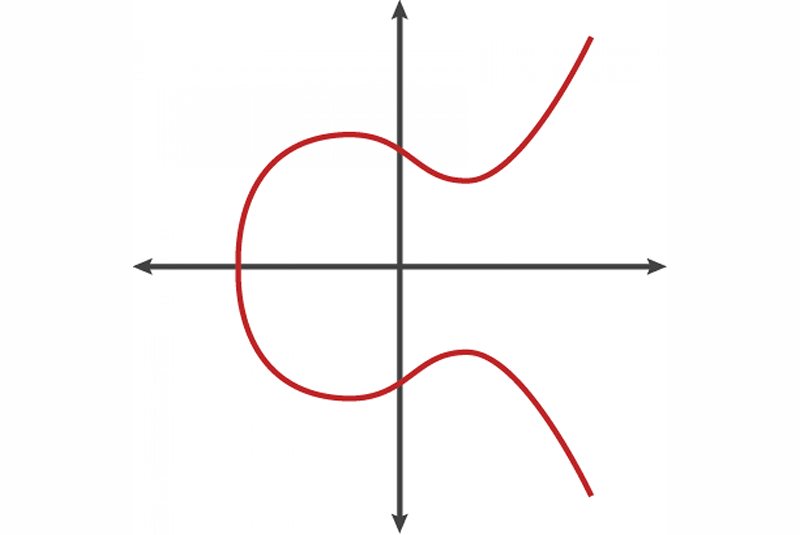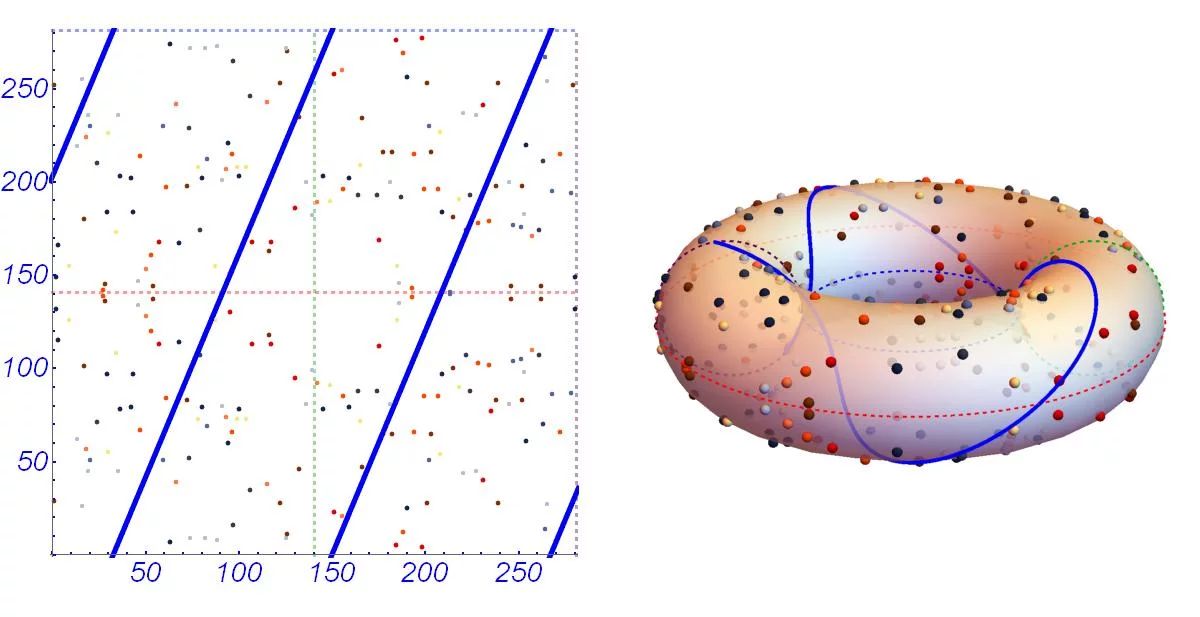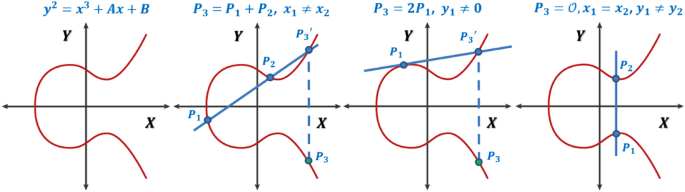
A generalized framework for elliptic curves based PRNG and its utilization in image encryption | Scientific Reports
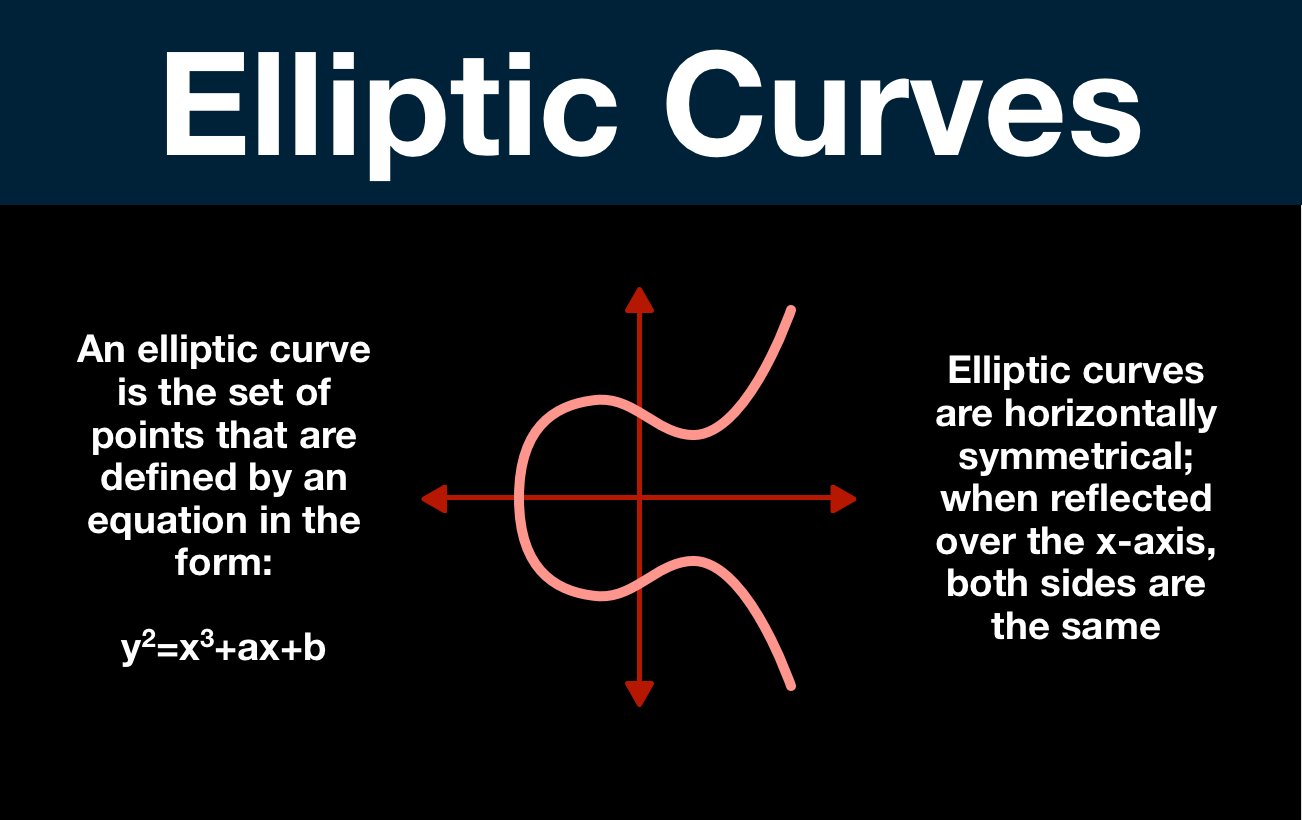
Tyrannosaurus Haym on Twitter: "(1/25) Cryptography Fundamentals: Elliptic Curve Cryptography Elliptic Curve Cryptography is (one of) our strongest cryptographic tools, vastly more secure than its predecessors. But... how does the moon math