Snyk on Twitter: "Find vulnerabilities in container images and fix them before pushing the image to @Docker Hub or any other registry. #docker #security #snyk https://t.co/NDZyFqgOpY https://t.co/sh26Z9Yrre" / Twitter

How to scan vulnerabilities for Docker container images — Part2 | by Luke Skywalker | System Weakness












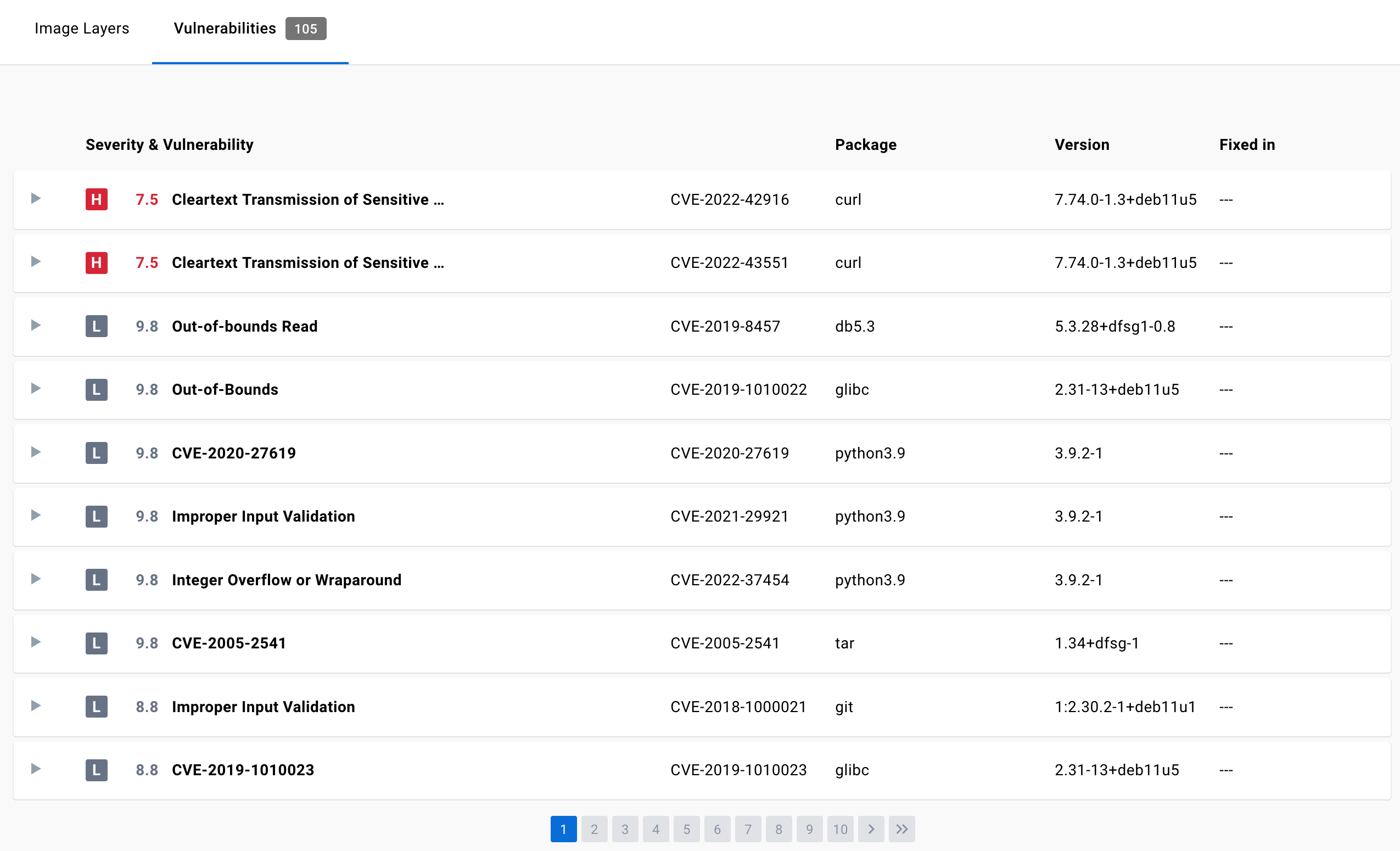
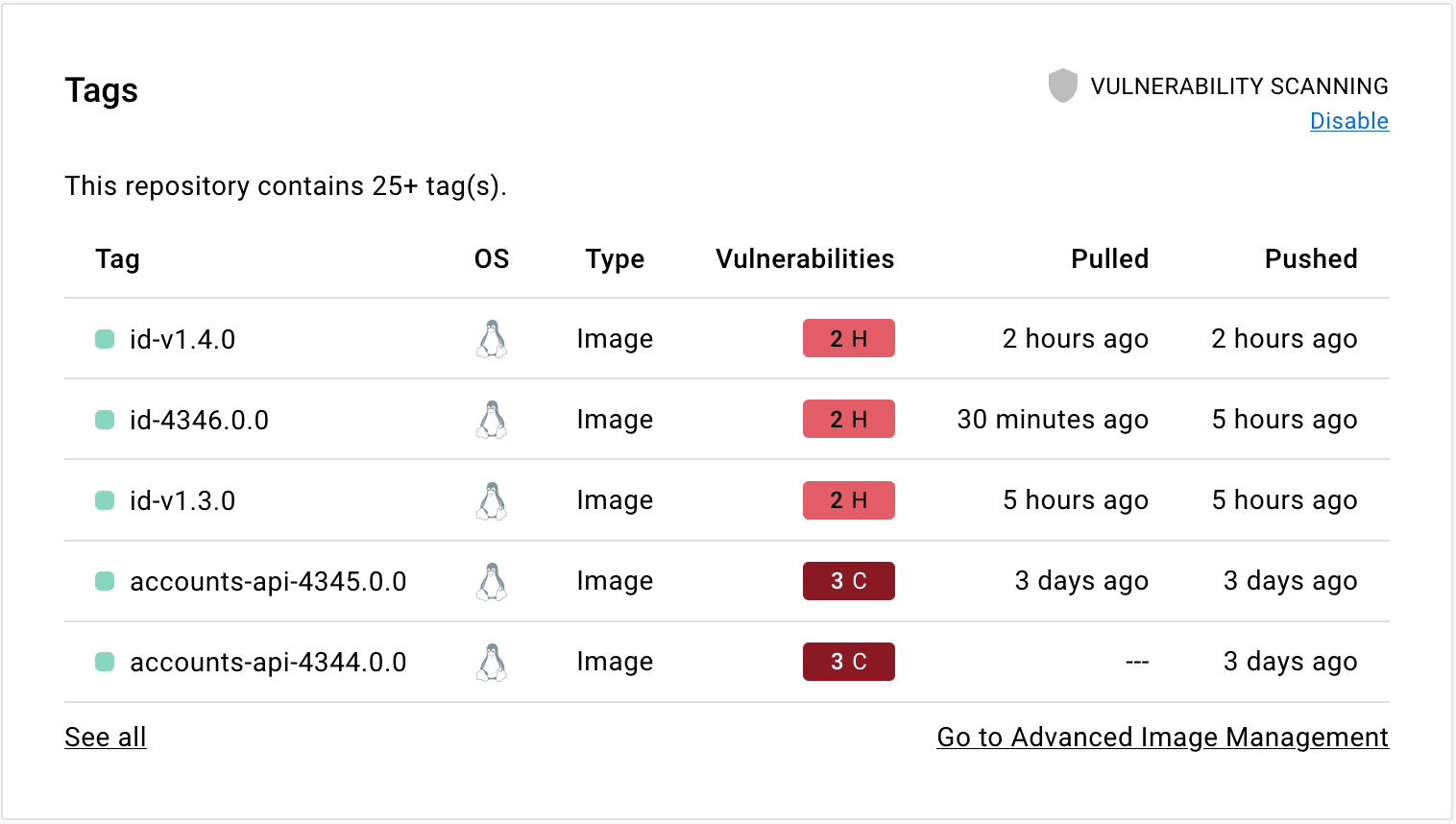




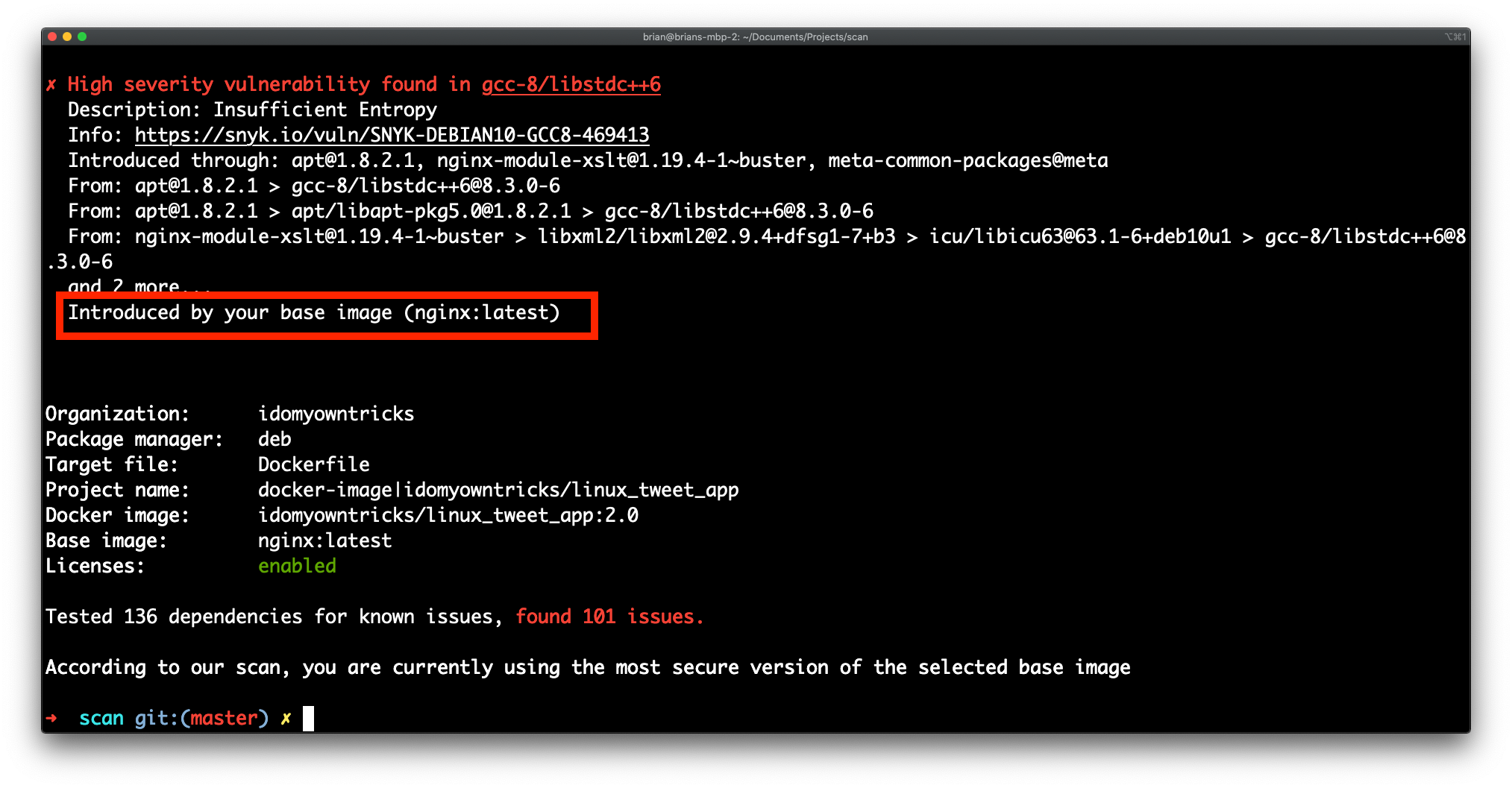
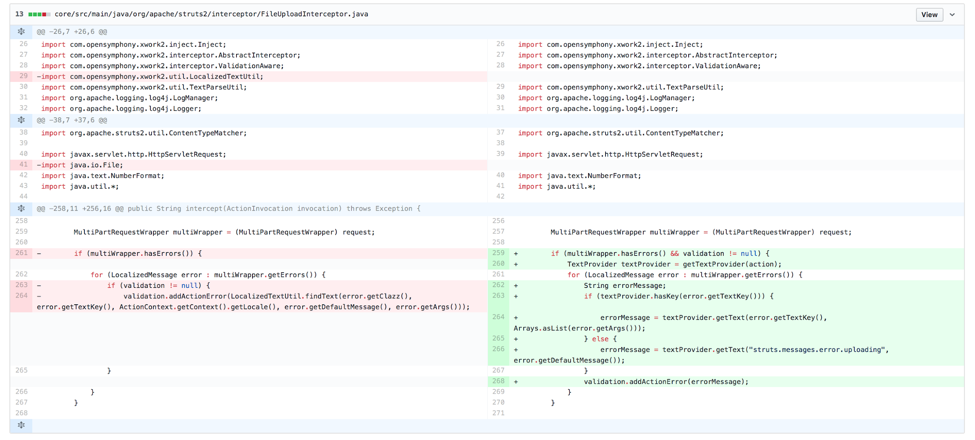
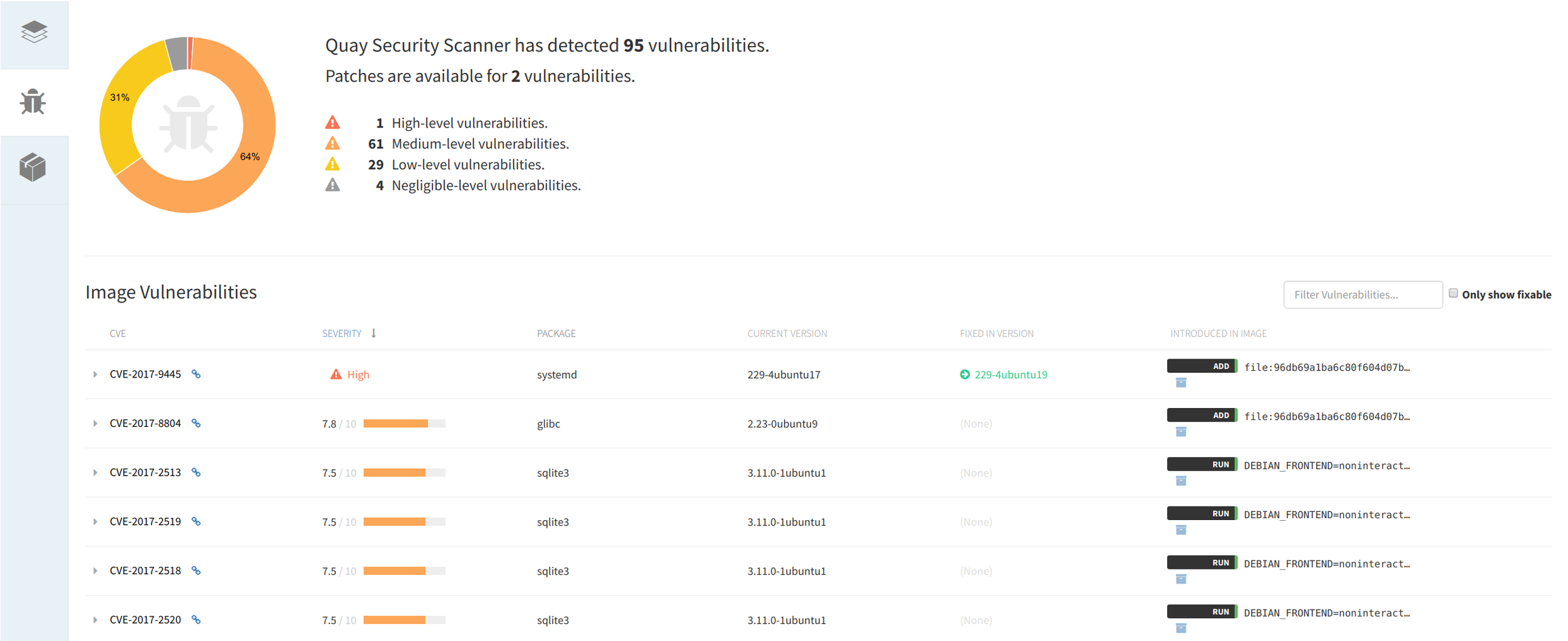
/filters:no_upscale()/news/2020/12/dockerhub-image-vulnerabilities/en/resources/1Screenshot%20from%202020-12-20%2014-54-56-1608456415853.png)
