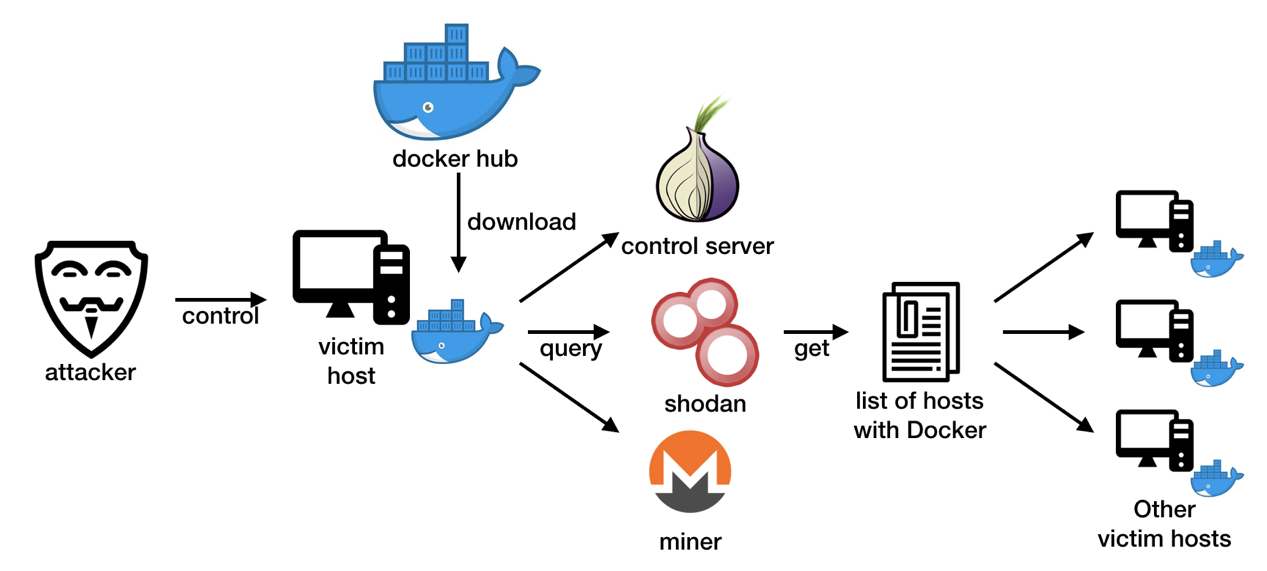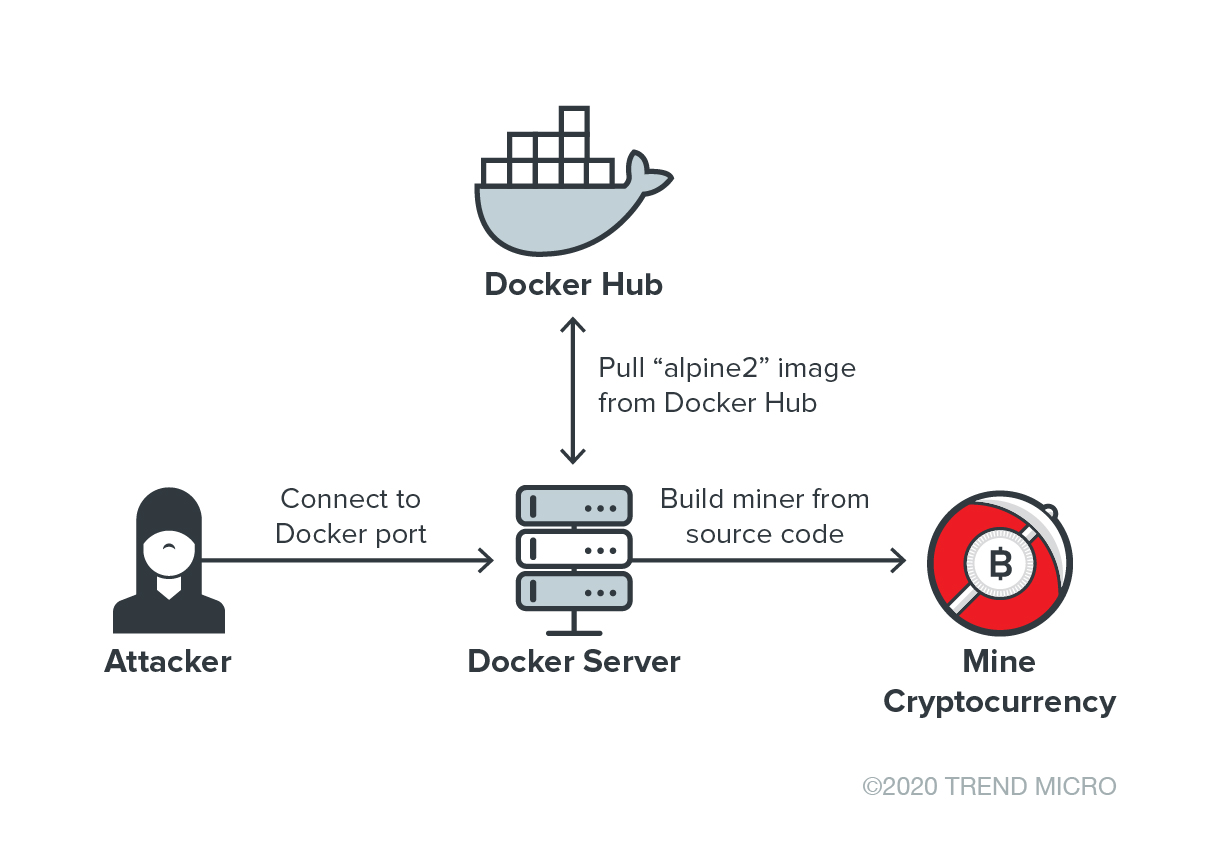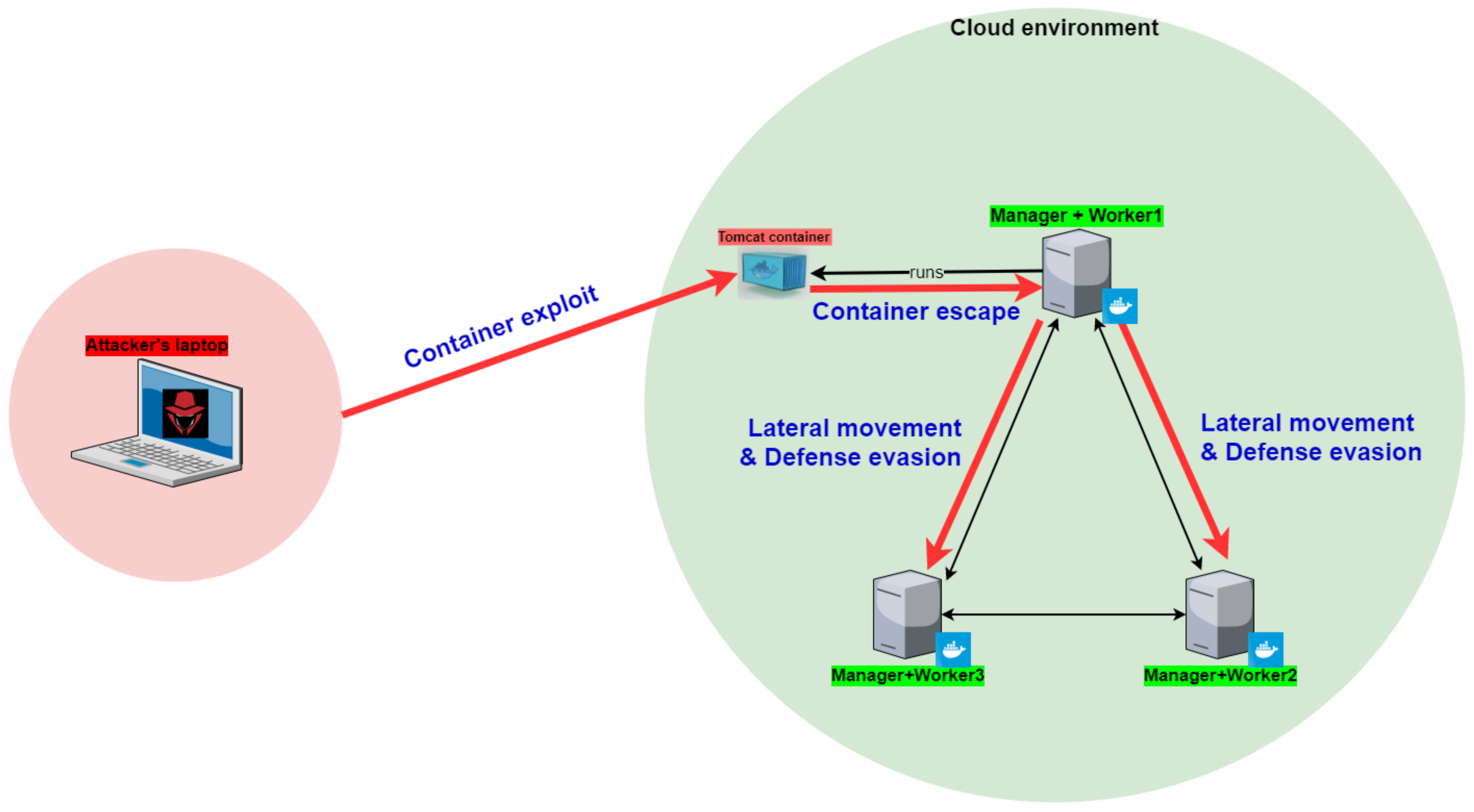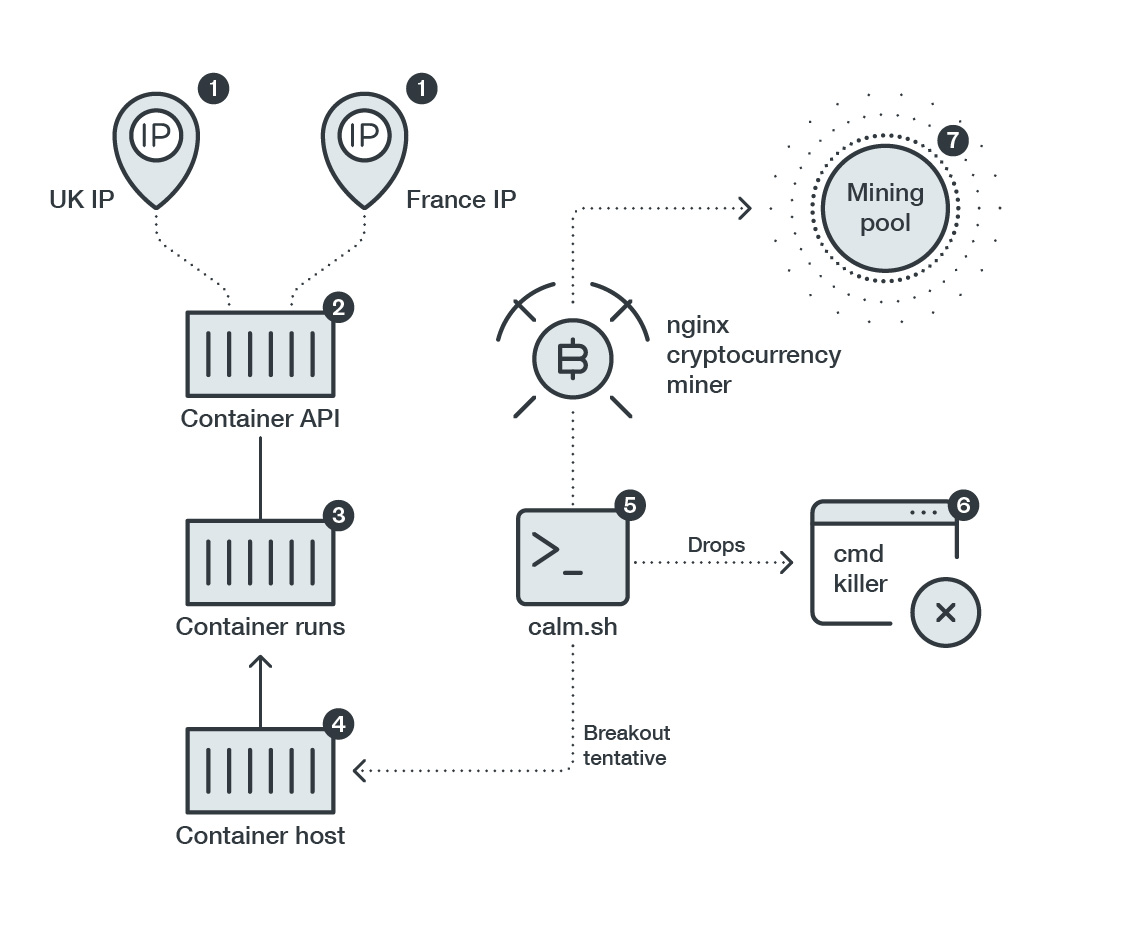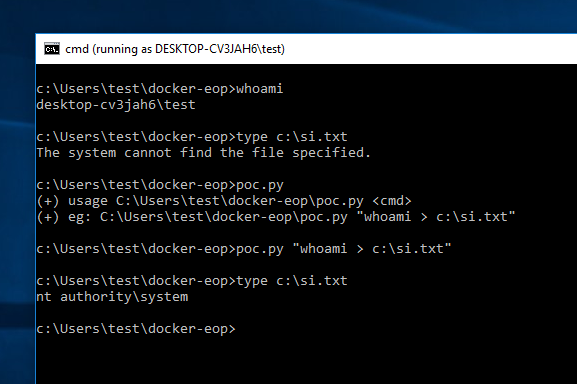
You can't contain me! :: Analyzing and Exploiting an Elevation of Privilege Vulnerability in Docker for Windows

Proof of Concept: Manually Escaping Privileged Docker Containers Without Exploiting Vulnerabilities - YouTube

Log4j for Dummies: How to Determine if Your Server (or Docker Container) Is Affected by the Log4Shell Vulnerability